APT42, which is believed to be affiliated with Iran’s government intelligence agency IRGC-IO, has been implicated in a series of social engineering attacks which target Western and Middle Eastern organizations. These attacks are performed using tactics such as spear-phishing and typo-squatting, to ultimately breach corporate networks and cloud environments.
According to Google Threat Analysts, the hackers use highly targeted malicious emails to infect organizations with two custom backdoors, known as “Nicecurl” and “Tamecat”. These backdoors facilitate command execution, data exfiltration and system manipulation on the victim’s environments.
Attack Process
These attacks begin with APT42 creating specially crafted online personas in the form of social media profiles, attempting to solidify the reputation of their social engineering attacks.
These online personas are often posing as journalists, NGO representatives, or event
organisers.
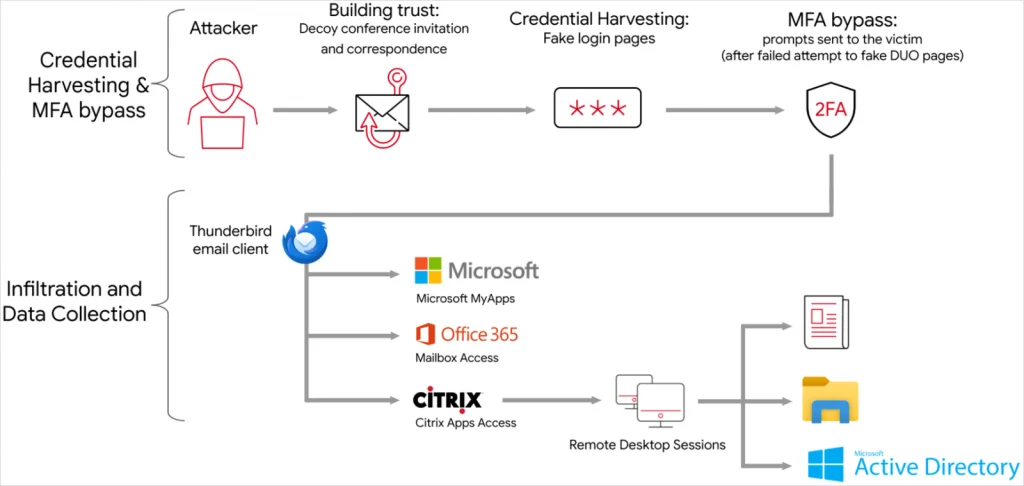
These online personas, along with domains that “typosquat” (use similar URLs to legitimate organizations) are then used to establish a rapport of email communications, to build trust with an employee of a victim organisation.
A link to a document, which is hosted on a file hosting service Dropbox, is then shared with the victim, including links to phishing pages of well-known services such as Google, Microsoft, or even specialized platforms tailored to the victim’s field of work.
These phishing sites not only steal the victim’s login credentials, but also multi-factor authentication (MFA) token, allowing the attacker to bypass a critical security measure.
After stealing account credentials and initial access to the environment is established, APT42 will then utilise various evasion techniques, such as limiting actions to built-in features and clearing browser history. In addition to this, they also use ExpressVPN nodes, Cloudflare-hosted domains, and VPS servers to make attribution difficult.
Backdoor Malware Execution
The two backdoors, named “Nicecurl” and “Tamecat” are each tailored for specific purposes within the attack.
Nicecurl, which is a VBScript backdoor can both install additional payloads from an external service, as well as perform command execution.
Tamecat, on the other hand, is a complex Powershell backdoor which executes PS code or C# scripts, allowing APT42 to perform a large variety of advanced techniques to aid in data-theft or system manipulation. Alarmingly, Tamecat is also able to obfuscate its external communications, and can update its configuration dynamically, making detection even more difficult.
These backdoors allow APT42 to remain focused on their primary goal; intelligence collection, while remaining undetected and leaving a minimal footprint.
A full list of the IOCs associated with this attack is visible on Google’s blog post.






