A significant number of free VPN applications, which were available on the Google Play Store, were recently discovered to secretly repurpose user’s devices as unwitting proxies for the use in cyber-crime.
The ‘PROXYLIB’ campaign utilized a code library to facilitate proxy functionality and was found to be present in over 28 applications on the Google Play store, 17 of which were marketed as Free VPN software.
The applications which were part of the ‘PROXYLIB’ campaign provided legitimate and functional VPN services to users on the surface. However, in the background, they were secretly registering the user’s entire device and by association, network to a residential proxy network, without the user’s knowledge or consent.
Residential proxies are often considered as the prime proxy choice among cyber-criminals, as they can appear as a home network, compared to regular data-centre proxies which will almost always indicate a proxy being used. This allows an attacker to bypass many access controls across a wide variety of security systems, since the network will not appear as part of a proxy network.
The use of residential proxies can have legitimate purposes, such as market research or SEO. However, cybercriminals often exploit residential proxies for malicious purposes like fraud, spamming, and phishing.
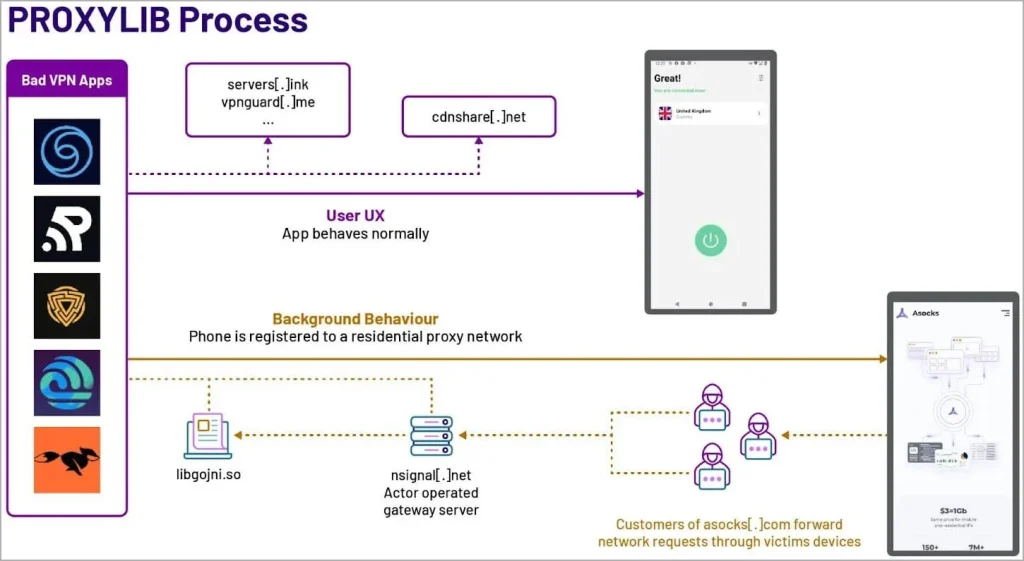
Most concerningly, HUMAN, a security team, attribute the malicious applications to the Russian proxy service provider known as ‘Asocks’, after connections were made to the website. Asocks is commonly promoted to cybercriminals for the purpose of malicious activity on hacking forums.
A full list of the 28 applications which utilized the PROXYLIB library is as follows:
- Lite VPN
- Anims Keyboard
- Blaze Stride
- Byte Blade VPN
- Android 12 Launcher (by CaptainDroid)
- Android 13 Launcher (by CaptainDroid)
- Android 14 Launcher (by CaptainDroid)
- CaptainDroid Feeds
- Free Old Classic Movies (by CaptainDroid)
- Phone Comparison (by CaptainDroid)
- Fast Fly VPN
- Fast Fox VPN
- Fast Line VPN
- Funny Char Ging Animation
- Limo Edges
- Oko VPN
- Phone App Launcher
- Quick Flow VPN
- Sample VPN
- Secure Thunder
- Shine Secure
- Speed Surf
- Swift Shield VPN
- Turbo Track VPN
- Turbo Tunnel VPN
- Yellow Flash VPN
- VPN Ultra
- Run VPN
Regarding containment for a device that has installed one of the listed apps, BleepingComputer recommends the following approach:
- Update the application to the newest version: This would ensure the PROXYLIB library would not be present, and therefore, will stop the proxying activity.
- Removal of the application: While the updated version may address the proxying
activity, uninstalling the application from affected devices eliminates the risk of possible malicious activity entirely.
The ‘PROXYLIB’ application outlines the importance of cautiousness and due diligence required by not only organizations and industry professionals, but also individual consumers. With constantly evolving threats, including the obfuscated nature of applications such as the ones as part of the PROXYLIB campaign, consumers of all levels may fall victim to having their network being used by criminals, entirely without their knowledge.






