This forensics challenge was part of the HTB Business CTF 2024: The Vault of Hope. I found this particular scenario both relevant and rewarding, so I thought it would be worth publishing a write-up.
Mitigation is a forensics challenge which involved analyzing a live linux environment, identifying a backdoor, and mitigating it to obtain a flag.
Challenge Description
Having now gathered all the intelligence, you are now making the final preparations to attack the vault! You connect back to your server to review some important evidence one last time! However, as soon as you connect you discover things are in complete disorder. You check the root directory and you find /root/backdoor.log, clearly evidence of an active backdoor, set in place to hinder your assault on the Vault! Eliminate the backdoor in order to continue with your plans! Note: A new line is added in the logfile approximately every minute indicating the status of the backdoor. Note 2: Connect to the server using SSH and root:toor as credentials. Note 3: You need to be connected to the CTF VPN in order to reach the server.
Initial Checks
The first steps taken were to learn some common Linux backdoor techniques, and where to find them. I found a great blog post on Linux Backdoors and Where to Find Them, which served as a guide for my initial checks of the environment.
I initially investigated the following aspects:
- SSH Keys (authorized_keys) and .bashrc
- MOTD (update-motd.d)
- Cronjobs
- SUID
- Running parent and child processes
However, the environment being analyzed did have some limitations. Many commands, such Crontab, would not work. Instead, I had to resort to manually inspecting the cronjob files on the system.
These intial checks were useful in ruling out some of the common forms of backdoor on Linux systems, however, no backdoor was able to be attributed from these analyzations.
Enumeration
Upon completing the initial checks, identifying the particular version of the environment was extremely important. This was done with the following command:
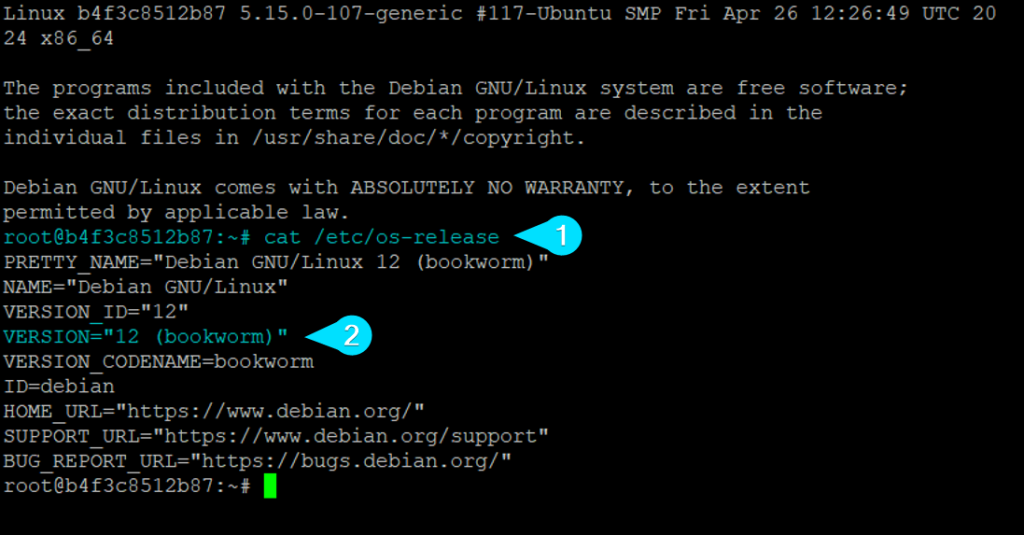
From the output of the os-release command, we know the system is running Linux 12 (bookworm).
The next step involves conducting Open Source Intelligence (OSINT) to uncover common vulnerabilities associated with Linux 12. A straightforward Google search using the term “Linux 12 Bookworm Backdoor” highlights one particularly significant vulnerability: The XZ Utils Backdoor. (CVE-2024-3094).
CVE-2024-3094 is a critical vulnerability identified in XZ Utils versions 5.6.0 and 5.6.1, resulting from a supply chain compromise. It specifically targets the liblzma component of XZ Utils library.
To determine if we are running a vulnerable version of XZ Utils, the following command is executed:
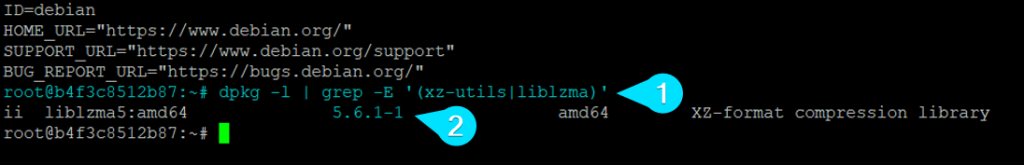
This output indicates that our XZ Utils is running version 5.6.1-1, which confirms our suspicion that the Linux environment is operating on a vulnerable version.
Mitigation
With the vulnerability now being identified, the vulnerable version of the application must be updated to eliminate the backdoor.
The latest version of Liblzma, 5.6.1+really5.4.5-1, contains the relevant fix for this CVE. We will download this version from Debian Packages, and install it on the linux system.
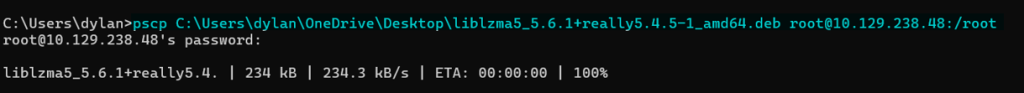
PSCP is used to aid in the process of transferring the updated package from another machine to the linux machine, since it does not have network access.
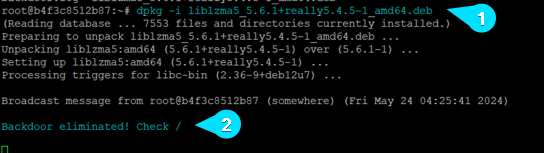
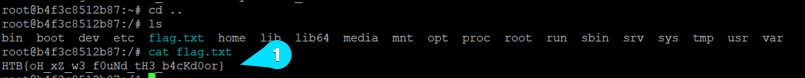
Upon installing the package, we are notified with a message stating “Backdoor eliminated! Check /”, and we have successfully retrieved the flag.






Смотреть здесь
http blacksprut ссылки