Black Basta, one of the most prominent ransomware operators, has recently been attributed to having breached over 500 organizations between April 2022 and May 2024. The gang has encrypted and stolen data from 12 critical infrastructure sectors, including healthcare organizations across North America, Europe, and Australia.
Black Basta, a Russian-speaking group, is believed to originate from the now-defunct Conti group, the successor of the Ryuk ransomware. It also has ties to FIN7, an advanced persistent threat group, due to overlapping C2 IP addresses.
The group operates as a Ransomware-as-a-Service (RaaS) model, where affiliates are paid a portion of the ransom upon a successful infection. Most alarmingly, Black Basta’s attacks seem highly targeted, with each infection having a tailored code depending on the organization being targeted. They also utilize double-extortion tactics, meaning organizations risk their data being encrypted and published publicly.
Attack Lifecycle
Black Basta’s attacks are incredibly complex and well-planned. Unique TTPs are utilized to infect the victim, spread laterally, execute the ransomware, and exfiltrate data. Various tools used during the attack, including QakBot, SystemBC, MimiKatz, CobaltStrike, and RClone, play a pivotal role in the entire attack process.
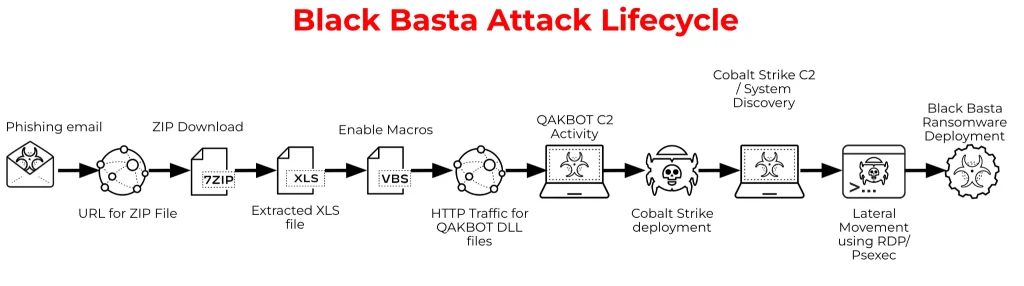
1. Initial Infection
The majority of attacks’ initial infection occurs from malicious zip files sent in phishing campaigns to target organizations. In numerous cases, Black Basta was also observed attempting to overwhelm email protection solutions by sending a large number of spam emails, which is often successful.
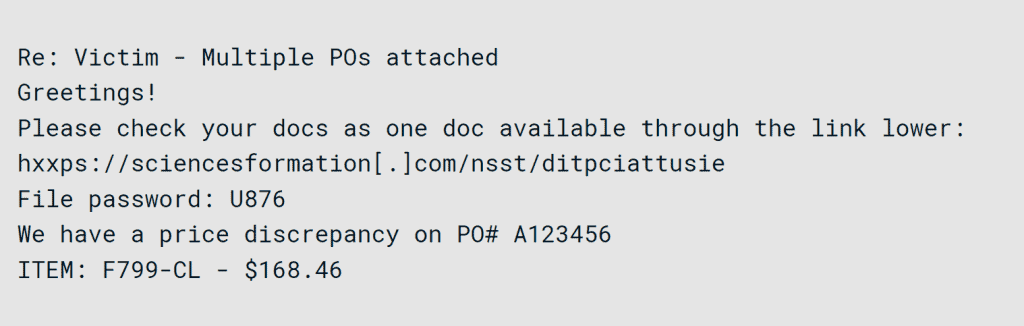
When the malicious file is executed, Javascript files are fetched remotely to compile and install Qakbot, a banking trojan with numerous capabilities. However, in these attacks, it is used to deliver further tooling.
SystemBC and CobaltStrike are then delivered via Qakbot to establish a C2 connection and conduct network reconnaissance.
2. Propogation and Persistence
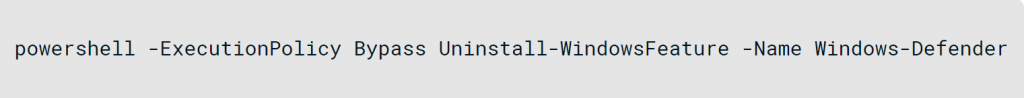
With Anti-Virus tools becoming standard and of utmost importance on all systems, it makes sense that the earliest scripts deployed by QakBot are batch scripts, which disable or remove anti-virus software like Windows Defender or Malwarebytes, further solidifying access by hindering detection.
In addition to these batch scripts, if remote access tools were not already installed during the initial infection phase, they are now installed and configured to maintain persistence. Some of these tools include AnyDesk, AteraAgent, or Splashtop.
3. Data Exfiltration and Encryption
After the previous phases establish access and lateral movement, two tools are used to exfiltrate data without the user’s knowledge. One of these is RClone, an open-source program used to transfer data. Black Basta also utilizes MimiKatz to extract Windows Administrator credentials.
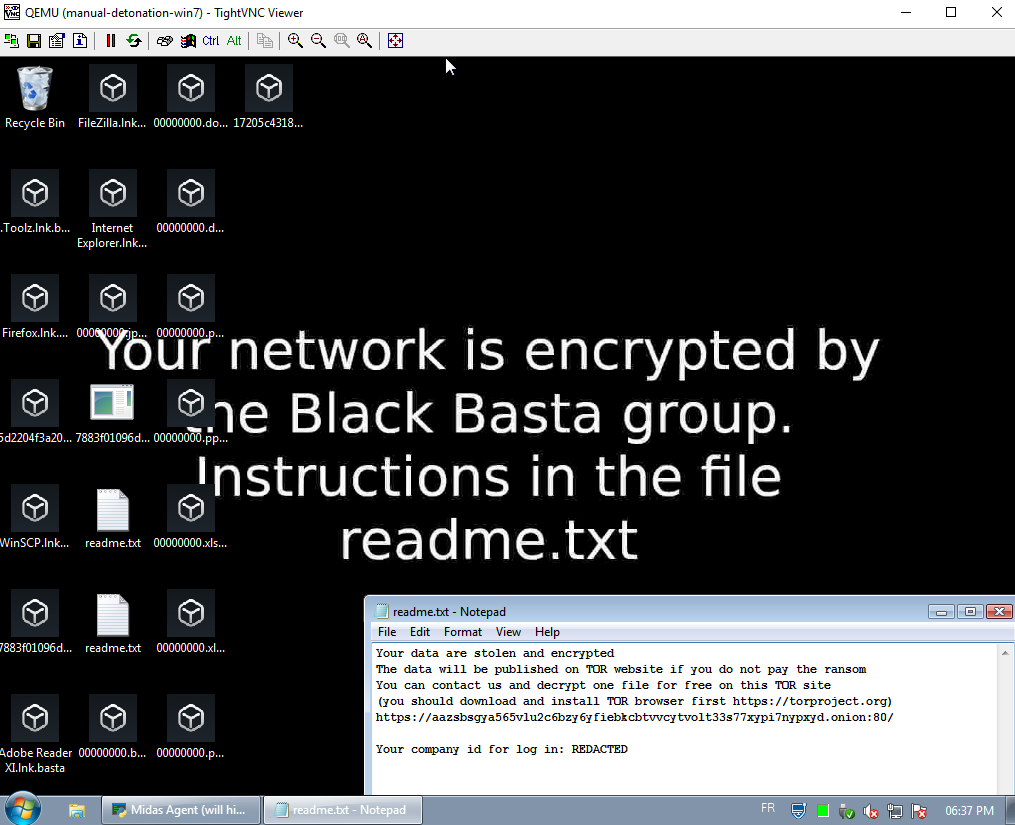
Once data is successfully extracted from the system, ransomware binaries are executed to encrypt the entire system, displaying a ransom note and rendering all files inaccessible.
Indicators of Compromise (IOCs)
Hundreds of indicators of compromise exist for the Black Basta Ransomware since each attack is tailored toward the intended victim. However, an example of some consistent IOCs are as follows:
| File Name | MD5 Hash | Purpose |
| av.bat | DD4816841F1BAFDC0482EFC933BA8FE5 | Script to remove Windows Defender |
| 1.bat | 5E601E8AA6A9A346E7907BA300EE1C3F | Script to remove MalwareBytes |
| UpdaterUISCC.exe | 325B90384EBDD794221C9A010C4A73B1 | SystemBC |
| <Random String> | 20D03F8272648FA3FD31E222B8E2220F | Ransomware Binary |
| <Random String> | AB79DBF72D25701F8703E0B5457A535B | Ransomware Binary |
| ILUg69ql1.bat | 95E196B9DE3C8E05B835B091B8EC1436 | Windows Defender removal script |
| ILUg69ql2.bat | 01FF5E75096FE6A8A45BFA9C75BFEB96 | Windows Defender removal script |
| ILUg69ql3.bat | 978D3DFDAB9CD0ED684ED4CCDCB3AAF4 | Windows Defender removal script |
| <Unknown> | 3635C0E80E526C9A92C26EF95BEA95F9 | QakBot Zip File |
| IP Address/URL | Comment |
| 104.243.42.239 | CobaltStrike C2 |
| 213.227.15.194 | CobaltStrike C2 |
| 155.138.194.253 | SystemBC IP |
| limitedtoday.com | CobaltStrike C2 Domain |
| thetrailbig.net | CobaltStrike C2 Domain |
For a full list of IOCs, visit TrendMicro and Rapid7.
Target Profiles
Black Basta’s typical target does vary quite widely; however, there are a few consistencies visible in the 500 organizations that have been confirmed to be victims of Black Basta.
Countries Affected
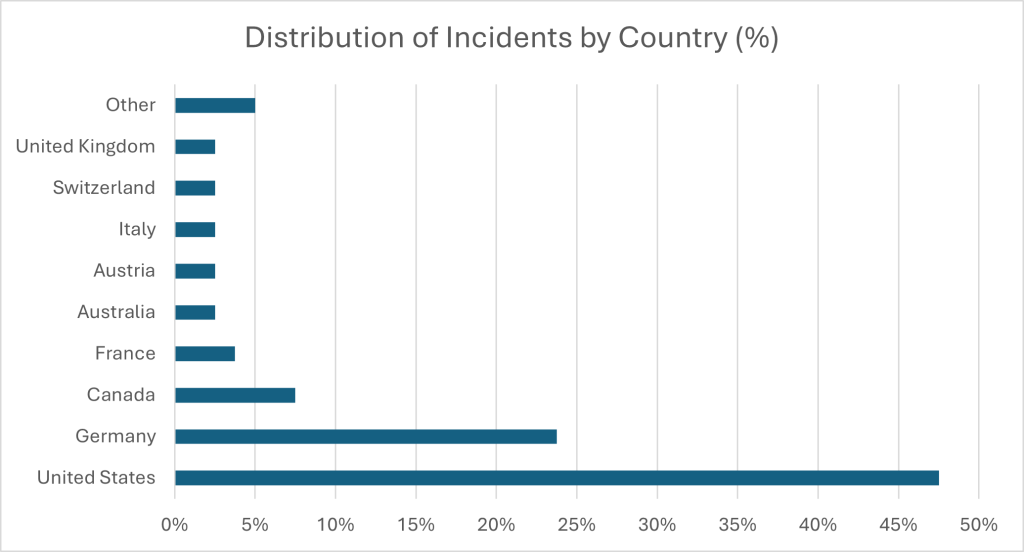
Unsurprisingly, USA organizations account for almost half of all targets.
Significantly, Black Basta’s strategic focus is on Western countries, particularly those in the Fourteen Eyes alliance. Disturbingly, countries with authoritarian-leaning governments, like Russia or China, remain untouched.
Industries Affected
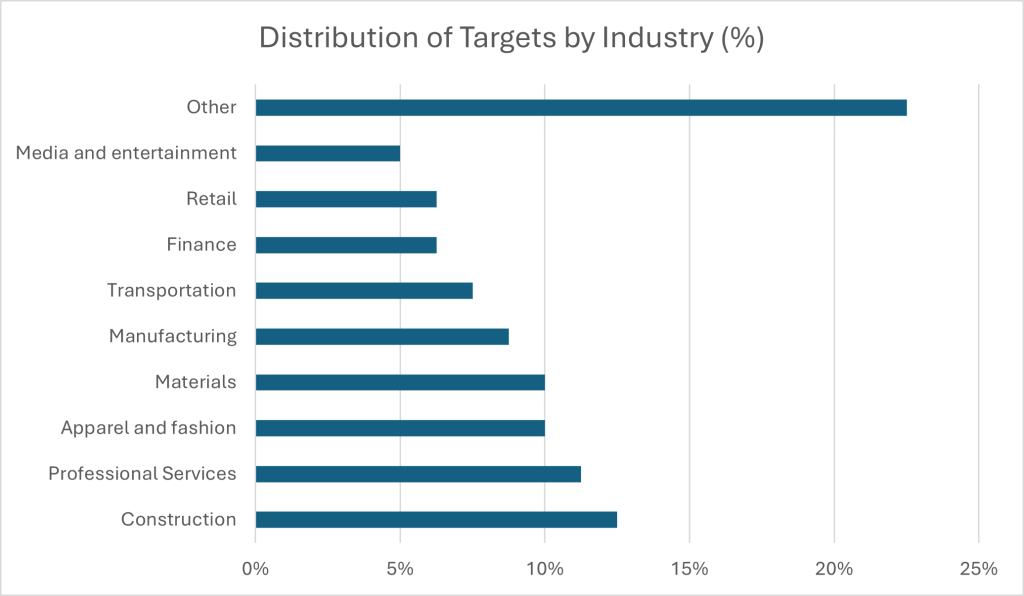
There seems to be a diverse range of industry targets, indicating that the group is not targeting any particular industry but any that suits its target profile.
However, based on recent news by BleepingComputer, we know that critical infrastructure is frequently targeted, and that health-care related organizations are a growing target of Black Basta.
Conclusion
Black Basta’s ransomware is highly complex and is a growing concern among US Federal Agencies due to its impact on critical infrastructure and health-care-related systems. As of late 2023, the gang has recorded a total of at least $100m in ransom payments; however, this amount could be much larger as of the current date.
In today’s rapidly evolving digital landscape, organizations of all sizes must recognize the importance of implementing a robust and comprehensive cybersecurity strategy. As the complexity and sophistication of cyber threats continue to grow, attackers show no discrimination in their targets, making it crucial for every organization, regardless of its size, to prioritize security. To effectively combat these threats, it is imperative to foster a culture of continuous education and awareness within organizations, ensuring that all stakeholders stay informed about the latest threats.






