In an alarming cyber security incident, an Australian man has been charged for conducting ‘evil twin’ Wi-Fi attacks on domestic flights and airports around Australia. This attack targeted unsuspecting travellers in Perth, Melbourne and Adelaide, and highlights the danger and vulnerabilities of connecting to public Wi-Fi networks.
An evil twin Wi-Fi network is a malicious wireless access point which mimics a legitimate or expected network’s name (SSID). For instance, the cybercriminal would create a Wi-Fi network, which they control, with a name such as QANTAS_FREE_WIFI, luring in unsuspecting users into connecting to it.
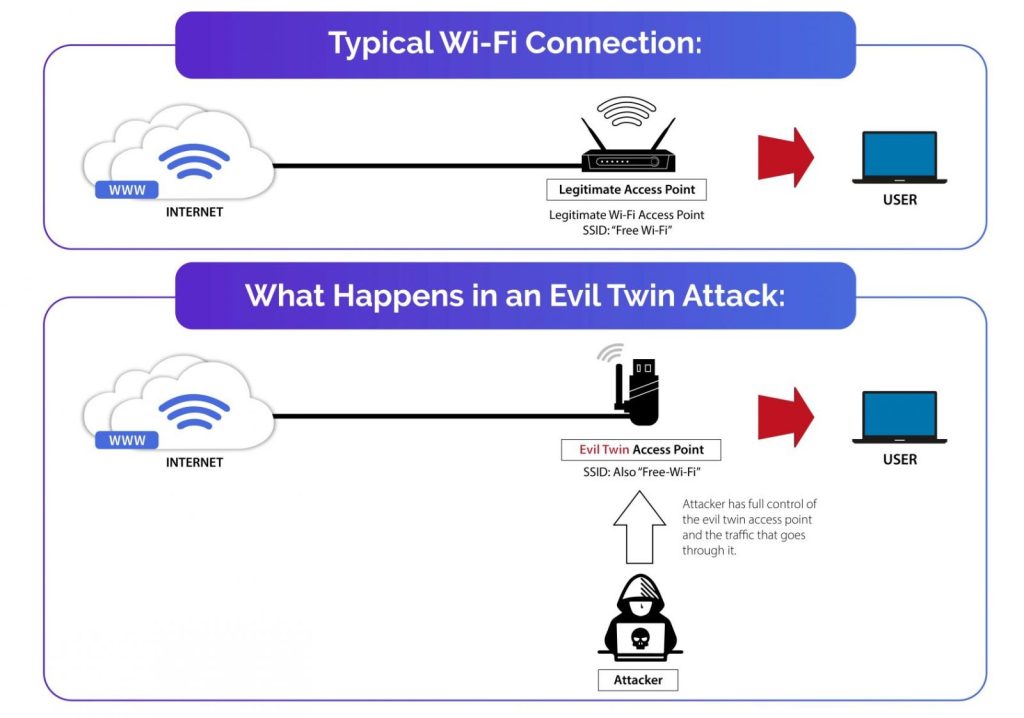
This type of attack may seem harmless on the surface, however, as witnessed in this case, the consequences can be sinister. When users connect to these malicious networks, they are often directed to fake login pages. Here, their credentials, such as email addresses and passwords are captured by the attacker.
The data that is collected through these attacks can be used for a variety of malicious purposes, including:
- Identity/Financial theft
- Unauthorised access to accounts
- Extortion attempts
The dangers of connecting to public Wi-Fi networks extend beyond evil twin attacks. Man-in-the-middle attacks and packet sniffing also pose a significant threat. These types of attacks allow attackers to intercept and capture sensitive information such as login credentials, financial details, and other sensitive information while users are connected to public WiFi networks unsuspectingly.
To stay safe from such attacks, it is highly recommended to adopt the following approaches:
- Be cautious when connecting to public Wi-Fi networks.
- Use a reputable VPN when using public Wi-Fi networks.
- Disable file sharing on untrusted networks.
- Avoid sensitive activities on public Wi-Fi.
- If possible, avoid public Wi-Fi networks all together.
Additionally, the AFP recommends anyone that connected to free WiFi networks in airport precincts or domestic flights to change their passwords, as well as report any suspicious activity on their accounts to Report Cyber.





